Broken authentication may be a basic security powerlessness that can uncover delicate information, compromise client accounts, and lead to unauthorized access. It happens when an assailant abuses shortcomings in an application’s authentication components, permitting them to bypass authentication and gain unauthorized access. In this web journal, we are going to dive into the significance of tending to broken authentication issues and give seven basic tips for investigating and settling them effectively.
Why Broken Authentication Matters
Broken authentication issues are a genuine concern for both businesses and clients. When cleared out unaddressed, they can lead to the taking after consequences:
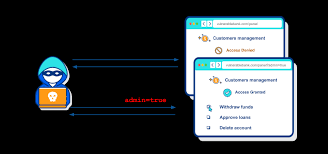
Unauthorized Get to: Aggressors can mimic genuine clients, picking up get to too touchy information and functionalities.
Data Breaches: Broken authentication can lead to information breaches, uncovering delicate client data like passwords, individual points of interest, and budgetary data.
Identity Robbery: Assailants can take client accreditations, driving to personality robbery and false activities.
Financial Misfortune: Unauthorized get to can result in money related misfortunes for both clients and businesses.
Reputation Harm: Information breaches and security episodes can seriously harm an organization’s notoriety and trustworthiness.
Now, let’s investigate seven significant tips for investigating and settling broken authentication issues.
- Routinely Overhaul Software and Libraries
Outdated software and libraries regularly contain known vulnerabilities that aggressors can misuse. Guarantee that your application’s authentication components, counting libraries and systems, are up-to-date. Routinely apply patches and security upgrades to dispose of known vulnerabilities.
- Implement Solid Password Policies
Weak passwords are a common section point for assailants. Implement solid secret word approaches that require clients to make complex passwords with a blend of capitalized and lowercase letters, numbers, and extraordinary characters. Energize secret word changes at customary intervals.
- Execute Account Lockout Mechanisms
To anticipate brute-force assaults on client accounts, actualize account lockout components. After a certain number of fizzled login endeavors, bolt the account incidentally or require client mediation to open it. This avoids aggressors from over and over speculating passwords.
- Utilize Session Administration Best Practices
Ensure that your application utilizes secure session administration hones. Sessions ought to have timeouts, and session tokens ought to be safely put away and transmitted. Actualize session obsession and session capturing avoidance instruments to ensure client sessions.
- Perform Customary Security Reviews and Testing
Conduct security reviews and infiltration testing to distinguish and address verification vulnerabilities proactively. Robotized checking apparatuses and manual testing can reveal issues that might not be clear amid development.
- Teach Clients approximately Security
Educate your clients about the significance of solid passwords, MFA, and secure online hones. Give assets and direction on keeping up secure account qualifications and recognizing phishing attempts.
Conclusion
Broken authentication issues posture a critical risk to the security of applications and user data. Ignoring these vulnerabilities can lead to unauthorized get to, information breaches, and reputational harm. By taking after the seven tips sketched out over, you’ll be able proactively address and troubleshoot broken authentication issues, upgrading the security of your applications and securing both your business and your clients. Keep in mind that security is a continuous preparation, and remaining watchful is basic within the ever-evolving scene of cybersecurity.