Cloud security alludes to the hones and methods planned to ensure cloud computing frameworks and information from unauthorized get to, burglary, or destruction.
As more organizations receive cloud-based arrangements for their IT foundation, guaranteeing the security of cloud situations has gotten to be progressively important.
Access control: Cloud providers actualize different get to control instruments to guarantee that as it were authorized staff have get to to cloud assets. These incorporate multi-factor confirmation, role-based get to control, and character and get to administration (IAM) policies.
Encryption: Encryption is an imperative portion of cloud security. Cloud providers utilize encryption to secure information in travel and at rest utilizing different encryption conventions such as SSL, TLS, and AES.
Network security: Cloud providers utilize different organize security measures, such as firewalls, interruption discovery and avoidance frameworks, and virtual private systems (VPNs), to protect cloud situations from unauthorized get to and cyber threats.
Data security: Cloud suppliers execute different information security measures, such as reinforcements, calamity recuperation, and information misfortune avoidance (DLP) arrangements, to guarantee the accessibility and keenness of information put away within the cloud.
Compliance: Cloud suppliers must comply with different industry-specific directions, such as HIPAA for healthcare organizations, and GDPR for companies that work within the European Union. As such, cloud suppliers actualize different compliance and reviewing forms to guarantee that they meet these regulations.
User instruction: Cloud security too includes teaching clients on best hones for utilizing cloud assets securely and safely. This incorporates preparing representatives on how to recognize and react to security dangers, and executing approaches to enforce good security practices.
In rundown, cloud security could be a complex and multifaceted field that requires a combination of specialized and organizational measures to ensure cloud situations from cyber dangers and information breaches.
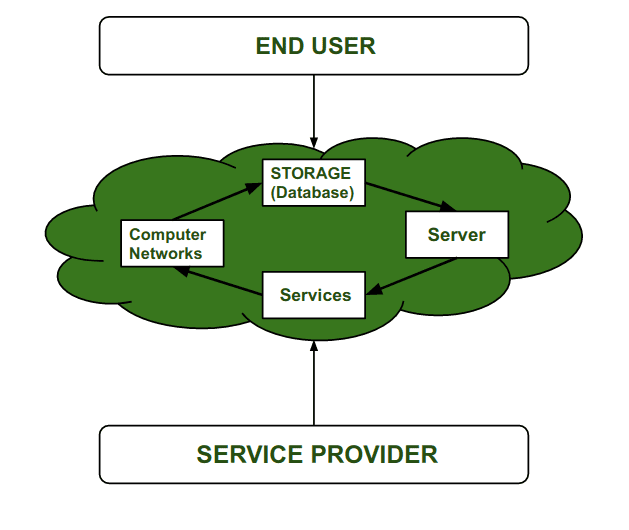
Understanding Cloud Security:
Understanding cloud security includes knowing the different components that make up cloud computing and the potential security dangers related with each component.
Cloud infrastructure: The fundamental foundation of cloud computing is composed of physical and virtual servers, capacity gadgets, and organizing gear. Security dangers related with cloud infrastructure incorporate information breaches, unauthorized get to, and denial-of-service (DoS) attacks.
Cloud applications: Cloud applications are web-based computer program programs that run on cloud infrastructure. Security dangers related with cloud applications incorporate software vulnerabilities, malware, and information breaches.
Cloud data: Cloud information alludes to information put away in cloud foundation or handled by cloud applications. Security dangers related with cloud data incorporate information breaches, information misfortune, and data leakage.
Cloud users: Cloud clients incorporate both representatives of the organization and third-party temporary workers or merchants who have get to to cloud assets. Security dangers related with cloud clients incorporate insider dangers, compromised qualifications, and unauthorized access.
To moderate these dangers, organizations can execute different security measures, including:
- Strong get to control components, such as multi-factor verification and role-based get to control.
- Data assurance measures, such as reinforcements, fiasco recuperation, and information misfortune anticipation (DLP) policies.
- Compliance and inspecting forms to guarantee that the organization meets industry-specific regulations.
- User instruction and preparing to guarantee that workers are mindful of and comply with security approaches and best hones.
Cloud Security Concerns:
Cloud security concerns are one of the greatest deterrents for organizations considering cloud selection. Here are a few of the beat cloud security concerns that organizations face:
Data breaches: Information breaches can happen when delicate information put away within the cloud is gotten to or stolen by unauthorized clients. This could incorporate individual data, mental property, and budgetary data.
Lack of control: When organizations move their IT framework to the cloud, they may feel that they lose control over their information and applications. This could cause concern for a few organizations, as they may not know where their information is put away or who has get to to it.
Compliance and administrative issues: Organizations must guarantee that their cloud supplier is compliant with significant controls such as HIPAA or GDPR. Non-compliance can result in lawful punishments, fines, and other lawful issues.
Insider dangers: Insider dangers, such as employees or temporary workers with get to to cloud assets, can posture a critical chance to cloud security. This could incorporate coincidental information introduction or malevolent activity.
Cloud supplier security: Cloud suppliers may involvement security breaches or vulnerabilities that can affect their clients. Organizations must guarantee that their cloud supplier has vigorous security measures in put to avoid these sorts of incidents.
Denial-of-service assaults: Cloud-based applications and administrations can be focused on by DoS assaults, which can disturb benefit and result in noteworthy downtime.To address these concerns, organizations must work with their cloud supplier to actualize vigorous security measures, such as encryption, get to control, and arrange security. They ought to too conduct customary security reviews and appraisals to identify vulnerabilities and address any security crevices. At last, organizations ought to guarantee that their workers are prepared on security best hones and approaches to play down the hazard of insider dangers.
Other Considerations in cloud security:
In expansion
to the beat cloud security concerns I specified prior, here are a few other critical contemplations in cloud security:
Shared obligation show: Numerous cloud suppliers take after a shared duty show, where they are capable for securing the cloud foundation, whereas the client is dependable for securing the applications and information they store within the cloud. Organizations must get it their duties beneath this show and take suitable measures to secure their information and applications.
Multi-tenancy: Cloud suppliers frequently utilize a multi-tenant design, where numerous clients share the same foundation. This may make security dangers, such as information spillage or unauthorized get to, on the off chance that not appropriately secured.
Shadow IT: Shadow IT alludes to the utilize of cloud administrations exterior of the organization’s affirmed IT frameworks. This may make security dangers, as these administrations may not be legitimately secured or overseen by the organization.
Security observing: Organizations ought to actualize strong security checking and logging capabilities to identify and react to security episodes. This incorporates checking arrange activity, application logs, and client activity.
Disaster recuperation: Cloud suppliers regularly offer catastrophe recovery services, but organizations must guarantee that their catastrophe recuperation plan is legitimately designed and tried to play down the chance of information misfortune or downtime within the occasion o Numerous organizatinof a disaster.
Third-party integrative:ns utilize third-party applications and administrations that coordinated with their cloud framework. These integrative can make security dangers on the off chance that not appropriately secured or managed.
To address these contemplations, organizations must take a all encompassing approach to cloud security, counting actualizing a comprehensive security procedure, conducting normal security appraisals, and remaining up to date on the most recent security dangers and best hones. Moreover, organizations ought to work closely with their cloud supplier and any third-party merchants to guarantee that their security prerequisites are met.
Access to World-Class Learning From Best Colleges with respect to cloud security:
There are a few ways to get to world-class learning from beat colleges with respect to cloud security:
Online courses: Numerous best colleges offer online courses on cloud security, such as cloud computing security, arrange security, and information security. These courses are regularly accessible through stages like Coursera, edX, or Udemy.
Professional advancement programs: Numerous beat colleges offer proficient advancement programs on cloud security, such as official instruction programs, certification programs, and workshops. These programs are planned for experts who need to develop their understanding of cloud security and pick up down to earth skills.
Conferences and occasions: Best colleges regularly have conferences and occasions on cloud security, where industry specialists, scholastics, and professionals come together to share information and best hones. These occasions offer an opportunity to memorize from the most excellent within the field and organize with peers.
Research papers and distributions: Best colleges conduct cutting-edge investigate on cloud security and distribute their discoveries in scholarly diaries and whitepapers. These distributions give important experiences into the most recent patterns and best hones in cloud security.Some of the best colleges advertising courses and programs on cloud security incorporate MIT, Stanford, Carnegie Mellon College, College of California, Berkeley, and Georgia Tech. Also, industry affiliations such as Cloud Security Union and SANS Organized offer preparing and certification programson cloud security.