In today’s world, data security is of vital significance, and it is basic that engineers take the essential steps to protect their users’ delicate data. With the expanding ubiquity of online exchanges, social media, and portable applications, information breaches have ended up more common, and it is more critical than ever to secure client information. The Java Cryptography Architecture (JCA) is one of the apparatuses accessible to designers to upgrade the security of their applications.
What is the Java Cryptography Architecture (JCA)?
The Java Cryptography Architecture could be a system that gives a set of APIs for actualizing cryptography in Java applications. It is portion of the Java Security system, which gives a comprehensive security foundation for Java applications. The JCA is built on best of the Java Security system and is utilized to supply cryptographic services, such as encryption and decoding, advanced marks, and key management.
Why is the JCA vital for Java security?
The JCA gives a standardized and secure way to perform cryptographic operations in Java applications. It guarantees that the cryptographic calculations utilized within the application are solid and secure, which the keys utilized to scramble and unscramble information are overseen safely. Also, the JCA gives a set of APIs that make it simple for developers to actualize encryption and decoding in their applications.
How does the JCA work?
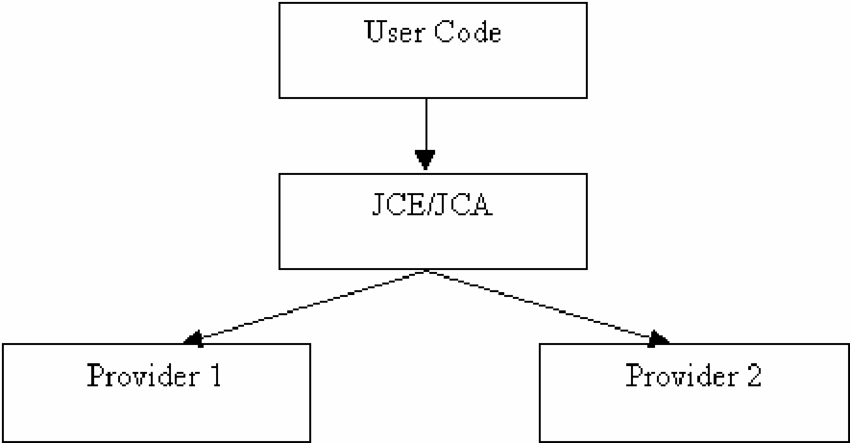
The JCA comprises of two primary components: the Java Cryptography Expansion (JCE) and the Java Cryptography Architecture Provider (JCAP). The JCE may be a set of classes that gives the center cryptographic usefulness, such as encryption and decoding, digital signatures, and key administration. The JCAP could be a supplier that executes the JCE APIs and gives get to to cryptographic calculations, such as AES, RSA, and SHA.
The JCA too gives a system for key management, which is basic for guaranteeing the security of scrambled information. The JCA gives a KeyStore API that permits engineers to store and recover keys safely, and a KeyGenerator API that can be utilized to produce unused keys for encryption and decoding.
Using the JCA in Java Applications
To utilize the JCA in a Java application, designers must to begin with include the JCE and JCAP to their application’s classpath. Once included, the engineer can utilize the JCE APIs to perform cryptographic operations, such as encryption and decryption.
For case, to encrypt a message utilizing the JCA, a developer can utilize the taking after code:
scss
Copy code
Cipher cipher = Cipher.getInstance(“AES/CBC/PKCS5Padding”);
cipher.init(Cipher.ENCRYPT_MODE, key);
byte[] encrypted = cipher.doFinal(plainText.getBytes());
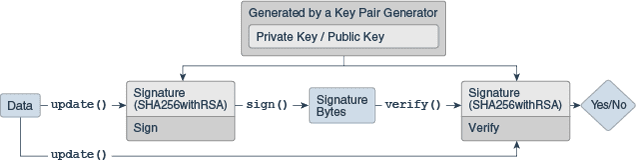
In this example, the developer creates a new instance of the Cipher class, which is used to perform cryptographic operations. The developer specifies the algorithm to use (AES/CBC/PKCS5Padding), initializes the Cipher object with the key to use for encryption, and then calls the doFinal() method to perform the encryption.
Conclusion
The Java Cryptography Architecture is an basic tool for upgrading the security of Java applications. It gives a set of standardized and secure APIs for performing cryptographic operations, as well as a system for key management. By using the JCA in their applications, developers can guarantee that their users’ delicate data is ensured from unauthorized get to and information breaches.
Here are some key points on Java Cryptography Architecture (JCA):
- JCA could be a system that gives a set of APIs for implementing cryptography in Java applications.
- It is portion of the Java Security system, which gives a comprehensive security foundation for Java applications.
- JCA gives a standardized and secure way to perform cryptographic operations in Java applications.
- It ensures that the cryptographic calculations utilized within the application are solid and secure, which the keys utilized to encrypt and decode information are overseen securely.
- JCA gives a set of APIs that make it simple for developers to actualize encryption and unscrambling in their applications.
- JCA comprises of two fundamental components: the Java Cryptography Expansion (JCE) and the Java Cryptography Architecture Provider (JCAP).
- The JCE could be a set of classes that gives the center cryptographic usefulness, such as encryption and unscrambling, advanced marks, and key management.
- The JCAP may be a supplier that executes the JCE APIs and gives get to to cryptographic calculations, such as AES, RSA, and SHA.
- JCA gives a system for key administration, which is basic for guaranteeing the security of scrambled data.
- The JCA can be utilized to execute a assortment of cryptographic administrations, counting encryption, unscrambling, advanced marks, and key administration.