The rise of cloud computing has brought many benefits to businesses, including scalability, flexibility, and cost-effectiveness. However, the use of cloud services also poses significant security risks, as sensitive data is stored on remote servers and accessed via the internet.
Access control is one of the essential components of cloud security. It refers to the measures put in place to ensure that only authorized users have access to sensitive data stored in the cloud. In this blog, we will discuss the importance of access control in cloud security and the strategies businesses can use to implement effective access control measures.
Importance of Access Control in Cloud Security
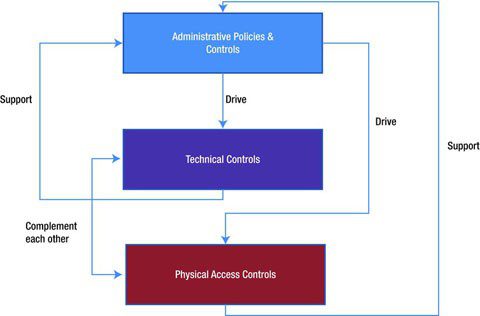
Get to control is critical in cloud security for a few reasons, including:
- Protecting Touchy Data – Get to control measures ensure that as it were authorized clients have get to to delicate information, ensuring it from unauthorized get to and potential breaches.
- Compliance – Numerous businesses have administrative necessities for the security of delicate information, and get to control measures are fundamental
in guaranteeing compliance with these regulations. - Preventing Insider Dangers – Get to control measures can too anticipate insider dangers, such as representatives or temporary workers with malevolent aim who may endeavor to get to delicate data.
- Maintaining Believe – Get to control measures illustrate to clients and partners that businesses are committed to ensuring their information, improving believe and notoriety.
Implementing Effective Access Control Measures
To execute successful get to control measures in cloud security, businesses ought to consider the taking after strategies:
Identity and Access Management (IAM) – IAM frameworks empower businesses to oversee client get to to cloud assets and information by doling out parts and authorizations based on work work, guaranteeing that as it were authorized clients have access.
Multi-Factor Authentication (MFA) – MFA gives an additional layer of security by requiring clients to supply extra verification components, such as biometrics or security tokens, in expansion to a password.
Encryption – Encryption may be a basic component of get to control in cloud security, because it ensures touchy information from unauthorized get to by scrambling it both in travel and at rest.
Regular Reviews and Audits – Standard audits and surveys of get to control measures can recognize potential vulnerabilities or shortcomings, empowering businesses to create essential alterations and improvements.
In conclusion, get to control may be a basic component of cloud security, ensuring delicate information from unauthorized get to, anticipating insider dangers, guaranteeing compliance, and keeping up believe. By executing compelling get to control measures, such as IAM, MFA, encryption, and normal reviews and surveys, businesses can guarantee the security and keenness of their cloud-based information and assets.