As increasingly businesses move online and depend on software systems to store delicate information, cybersecurity has gotten to be an progressively imperative concern. In today’s risk scene, it isn’t sufficient to basically execute security measures and hope for the finest. Instep, it is vital to proactively recognize and address potential vulnerabilities in software systems some time recently they can be misused by noxious actors. .
What is Penetration Testing?
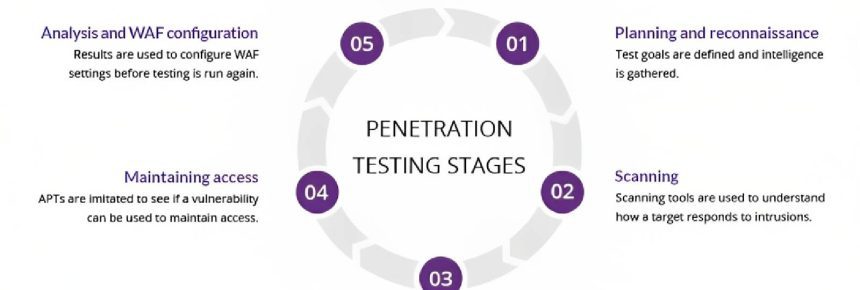
Penetration testing, moreover known as write testing, may be a cybersecurity hone that involves simulating a cyber assault against a software system to distinguish vulnerabilities and shortcomings. It is ordinarily carried out by a prepared and certified cybersecurity proficient, who will endeavor to misuse vulnerabilities in a controlled environment to see how distant they can enter the system.
The objective of infiltration testing is to distinguish shortcomings in a software system some time recently they can be abused by malicious on-screen characters. By doing so, businesses can take proactive measures to strengthen their security resistances and avoid potential information breaches, system downtime, or other security occurrences.
Why is Penetration Testing Vital for Software Security?
There are a few key reasons why penetration testing is an basic component of software security:
Identifying Vulnerabilities: Entrance testing is outlined to recognize vulnerabilities and shortcomings in a package that may well be misused by assailants. By distinguishing these vulnerabilities, businesses can take steps to address them and minimize the chance of a effective cyber attack.
Proactive Security: Penetration testing could be a proactive approach to software security that helps businesses remain one step ahead of potential assailants. Instead of holding up for an assault to happen and after that attempting to relieve the harm, businesses can distinguish and address vulnerabilities some time recently they are exploited.
Compliance: Numerous businesses are subject to administrative compliance necessities that order normal security testing, counting entrance testing. Falling flat to comply with these necessities can result in exorbitant fines and harm to a business’s reputation.
Cost-Effective: Whereas the taken a toll of a penetration test can change depending on the complexity of the system being tried, it is by and large much less costly than the taken a toll of a information breach or other security occurrence. By contributing in normal infiltration testing, businesses can spare cash within the long run by maintaining a strategic distance from expensive security episodes.
Best Practices for Penetration Testing
To guarantee the adequacy of entrance testing, it is vital to take after best practices, including:
Define Scope: Some time recently conducting a penetration test, it is imperative to characterize the scope of the test, counting what systems will be tried, what sorts of assaults will be recreated, and what level of get to the tester will have. Penetration testing ought to as it were be carried out by a certified cybersecurity proficient with experience in conducting tests on comparative systems.
Document Comes about: It is vital to report the comes about of a penetration test, counting vulnerabilities distinguished and remediation recommendations.
Address Vulnerabilities: Once vulnerabilities are recognized, it is vital to require provoke activity to address them and strengthen security defenses.
Conclusion
In today’s danger landscape, it is fundamental to require a proactive approach to software security. Entrance testing could be a important device for identifying vulnerabilities and shortcomings in program systems some time recently they can be misused by aggressors. By contributing in normal infiltration testing and taking after best hones, businesses can fortify their security protections and minimize the hazard of a exorbitant security occurrence.