Java, a broadly utilized programming dialect, has picked up notoriety due to its stage freedom and flexibility. Be that as it may, it has moreover confronted its reasonable share of security challenges over a long time. In this web journal, we’ll dive into the best seven realities around Java security issues and investigate the reasons behind its notoriety for vulnerabilities.
Java, created by Sun Microsystems (presently possessed by Prophet Organization), has ended up a principal dialect for web and application improvement. Its “Type in Once, Run Anyplace” capability permits designers to make computer program that can run on different stages. Be that as it may, Java’s notoriety moreover makes it an appealing target for cyber aggressors. Let’s investigate the beat seven truths approximately Java security issues.

Fact 1: Java’s Predominance Makes It a Prime Target
Java’s broad utilization in endeavor applications, web browsers, and versatile gadgets makes it a prime target for cybercriminals. As Java Virtual Machines (JVMs) are display on various frameworks, abusing vulnerabilities in Java can possibly affect millions of clients. Assailants frequently look for out broadly utilized innovations to maximize the reach of their noxious activities.
Fact 2: Past Vulnerabilities Wait in Obsolete Installations
The bequest of Java vulnerabilities proceeds to posture a hazard. Numerous organizations and people fall flat to upgrade their Java establishments routinely, taking off obsolete and uncertain adaptations in utilize. Cybercriminals misuse these unpatched vulnerabilities to pick up unauthorized get to to frameworks or convey malware.
Fact 3: Applet Security Risks
Java applets, once a prevalent way to upgrade web interactivity, have experienced noteworthy security challenges. Applets can run with lifted benefits, which implies they have get to to a user’s framework assets. This benefit level makes security dangers in case pernicious applets are executed, possibly driving to information burglary or framework compromise.
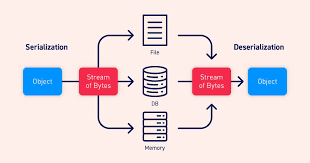
Fact 4: Serialization Vulnerabilities
Java’s serialization component permits objects to be changed over into byte streams and reproduced afterward. Be that as it may, this include can be misused by aggressors to execute self-assertive code on a framework. Serialization vulnerabilities have been a repeating issue in Java’s security landscape.
Fact 5: Unsigned Code and Security Risks
Java permits the execution of unsigned code, which presents security dangers. Unsigned applets or applications can run without client assent, possibly driving to the execution of noxious code. This highlight has been manhandled by aggressors to disperse malware and perform drive-by downloads.
Fact 6: Insufficient Client Input Validation
Insecure coding hones, such as insufficient client input approval, can lead to security vulnerabilities in Java applications. Disappointment to approve client inputs legitimately can result in code infusion assaults, such as SQL infusion or cross-site scripting (XSS), compromising the security of the application and the fundamental system.
Fact 7: Complex Security Model
Java’s security demonstrate, whereas outlined to be vigorous, can be complex and troublesome to oversee viably. Misconfigurations or mistaken assumptions of security highlights can lead to unintended vulnerabilities. Engineers and framework chairmen must have a comprehensive understanding of Java’s security components to dodge potential pitfalls.

Why Does Java Have So Numerous Security Issues?
The tall number of security issues related with Java can be ascribed to different factors:
Popularity and Focusing on:
As said prior, Java’s predominance makes it an appealing target for assailants. The more broadly utilized a innovation is, the more likely it is to confront security threats.
Legacy Code and Obsolete Establishments:
Bequest code and obsolete establishments are a critical challenge in keeping up a secure Java environment. Disappointment to upgrade frequently uncovered frameworks to known vulnerabilities.
Inherent Complexity:
Java’s flexibility and broad libraries make it capable but complex. Complexity frequently presents potential security shortcomings that might not be quickly apparent.
Insecure Coding Hones:
Engineers may accidentally present security vulnerabilities through uncertain coding hones. Insufficient input approval, inappropriate dealing with of client information, and other coding botches can lead to exploitable weaknesses.
Historical Vulnerabilities:
A few security issues may stem from plan choices or choices made within the early days of Java, driving to long-standing vulnerabilities.
Conclusion
Java, a broadly received programming dialect, has confronted its share of security challenges over the a long time. Its notoriety, complex security demonstrate, and past vulnerabilities contribute to its notoriety for security issues. Be that as it may, proactive measures, such as opportune overhauls, secure coding hones, and client mindfulness, can essentially moderate these dangers. Java remains a vigorous and flexible dialect, and with due constancy, its security can be viably kept up.