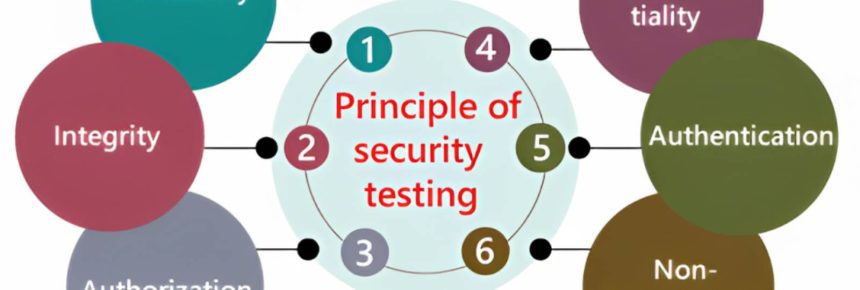
Analyzing Security Test Cases and scenario data can be a complex process, but it is crucial for identifying vulnerabilities and ensuring Security Test Cases of a system or application. Here are some steps to help explore the complexities of Security Test Cases and scenarios:
Understand Security Test Cases :
Before diving into the analysis, it is vital to have a clear understanding of the destinations of the security testing. What are the specific goals? What aspects of security are being tested? This clarity will guide your analysis and help you center on the relevant areas.
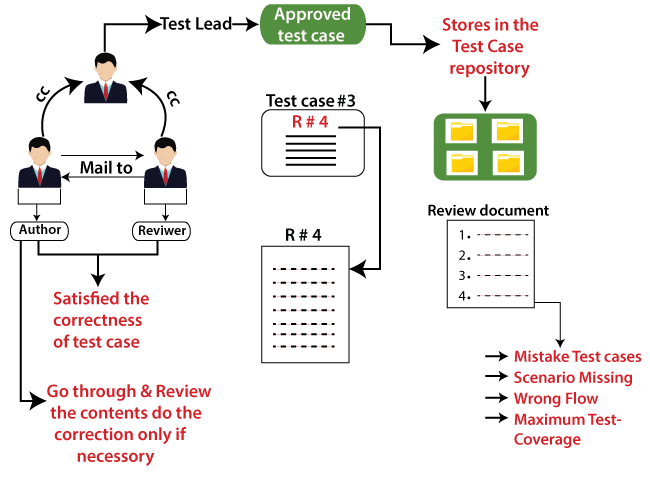
Review Test Case Documentation:
Begin by checking on the test case documentation given. Get it the scope of each test case, the anticipated behavior, and the security controls being tried. This will assist you pick up understanding into the particular test scenarios and the comparing data.
Identify Test Scenarios:
Analyze the test cases to recognize the distinctive test scenarios being assessed. Each situation speaks to a particular circumstance or condition that may possibly uncover vulnerabilities. Gather comparative scenarios together to encourage analysis.
Assess Test Information:
Look at the test information related with each situation. Test information incorporates inputs, setups, organize conditions, and client parts, among others. Distinguish the significant information components that may affect security and get it how they associated with the framework beneath test.
Evaluate Security Controls:
For each test scenario, assess the security controls in put. Review the usage of authentication mechanisms, get to controls, encryption, input validation, and other security measures. Identify any potential weaknesses or crevices in the security controls.
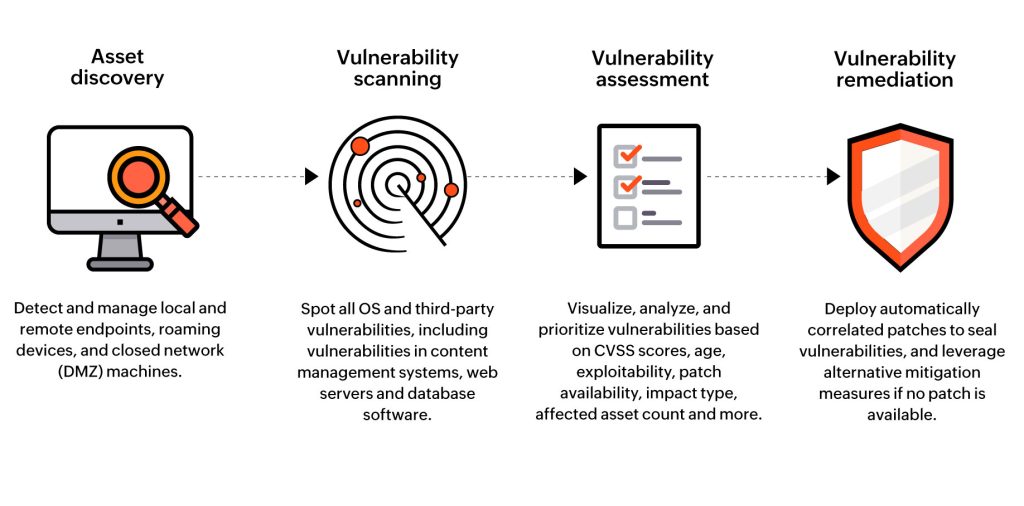
Analyze Potential Vulnerabilities:
Based on the recognized test scenarios, information components, and security controls, analyze the potential vulnerabilities that will emerge. Consider both known vulnerabilities and potential modern dangers. Explore for issues such as infusion assaults, benefit heightening, cross-site scripting, or delicate information exposure.
Prioritize Dangers:
Prioritize the distinguished vulnerabilities based on their seriousness, affect, and probability of abuse. Center on high-risk vulnerabilities that may have critical results in case abused. This prioritization will offer assistance direct remediation efforts.
Propose Remediation Activities:
Based on the examination, propose particular remediation activities for each distinguished helplessness. These activities seem incorporate code fixes, arrangement changes, extra security controls, or upgrades to security approaches and strategies. Give clear and significant recommendations.
Communicate Discoveries:
Plan a comprehensive report summarizing the investigation, counting the recognized vulnerabilities and prescribed remediation activities. Clearly communicate the dangers, potential impacts, and the criticalness of tending to each defenselessness. Share the report with pertinent partners, such as designers, analyzers, extend supervisors, and security teams.
Monitor Advance:
Track the advance of remediation endeavors and guarantee that the recognized vulnerabilities are tended to. Take after up with partners to guarantee the suggested activities are actualized successfully. Perform retesting as fundamental to approve the viability of the remediation measures.
Remember that security testing is an iterative prepare, and persistent advancement is key. Learn from each examination and apply those bits of knowledge to future test cases and scenarios to upgrade the security pose of the framework or application. Routinely overhaul and adjust your investigation approach to remain current with advancing security dangers and best hones.