Reverse engineering is a fascinating field that involves unraveling the inner workings of a product, system, or technology to understand its design, functionality, and operation. Often associated with software and hardware analysis, reverse engineering has numerous applications across various industries, including cybersecurity, engineering, manufacturing, and intellectual property protection. In this blog, we delve into the world of reverse engineering, exploring its techniques, benefits, and ethical considerations.
What is Reverse Engineering?
- 1.1 Defining Reverse Engineering:
- Reverse engineering explained in simple terms.
- Differentiating it from traditional engineering processes.
- Overview of the objectives and outcomes of reverse engineering.
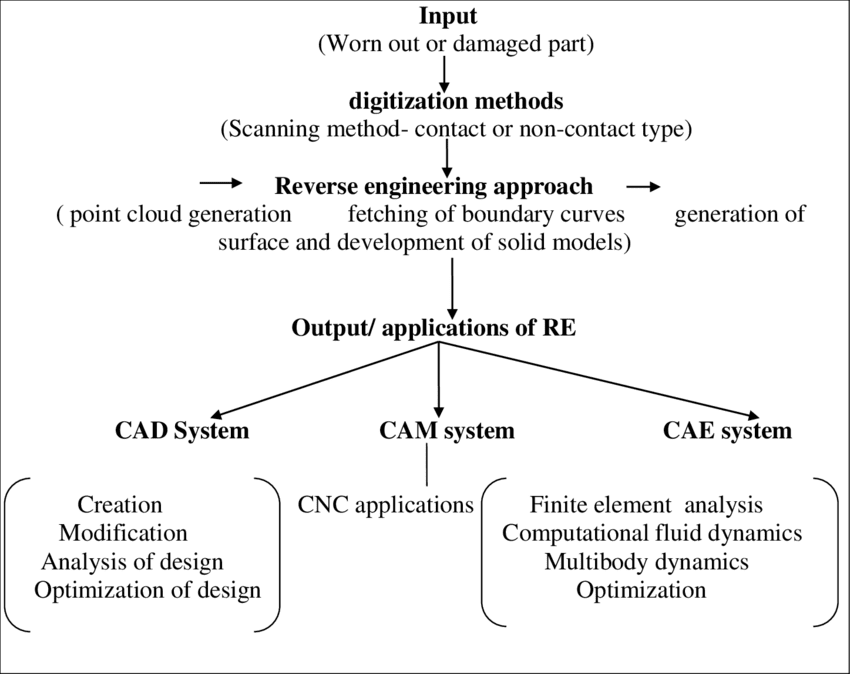
Applications of Reverse Engineering:
- Reverse engineering in software development.
- Hardware analysis and improvement through reverse engineering.
- Intellectual property protection and infringement investigations.
- Legacy system migration and documentation.

Techniques and Tools:
- 2.1 Disassembling and Decompiling:
- Breaking down compiled software code to understand its structure and logic.
- Popular disassembling and decompiling tools used in reverse engineering.
2.2 Debugging and Runtime Analysis:
- Using debuggers to step through code execution and analyze program behavior.
- Profiling and monitoring runtime processes for deeper insights.
2.3 Reverse Engineering Hardware:
- Utilizing schematics, circuit analysis, and datasheets to understand hardware designs.
- Tools and equipment commonly employed in hardware reverse engineering.
2.4 Reconstructing Designs:
- Building high-level representations from low-level analysis results.
- Techniques for generating software flowcharts, UML diagrams, and hardware schematics.
Benefits and Practical Applications:
- 3.1 Enhancing Security and Vulnerability Analysis:
- Identifying and patching security flaws in software and systems.
- Strengthening cybersecurity measures through proactive analysis.
3.2 Product Improvement and Innovation:
- Understanding competitors’ products to enhance your own.
- Uncovering hidden features or design flaws for product refinement.
- Inspiring innovation through analysis and modification of existing solutions.
3.3 Intellectual Property Protection:
- Detecting and proving patent or copyright infringement.
- Defending intellectual property rights through reverse engineering analysis.
3.4 Legacy System Understanding and Migration:
- Reverse engineering outdated or undocumented systems for migration or maintenance.
- Preserving critical knowledge and ensuring continuity in evolving technologies.
Ethical Considerations:
- 4.1 Legal and Ethical Boundaries:
- Understanding the legal frameworks governing reverse engineering in different countries.
- Navigating ethical dilemmas regarding proprietary information and rights.
4.2 Responsible Disclosure and Collaboration:
- Balancing the need for security with responsible disclosure of vulnerabilities.
- Promoting ethical collaboration between researchers, developers, and manufacturers.
4.3 Ethical Hacking and Bug Bounty Programs:
- The intersection of reverse engineering and ethical hacking.
- Bug bounty programs as a platform for responsible vulnerability disclosure.
Conclusion:
Reverse engineering is an invaluable process that allows us to unlock the secrets hidden within complex technologies. By exploring the techniques, tools, and applications of reverse engineering, we can better understand its significance in various industries. As we navigate the ethical considerations surrounding this field, it is crucial to strike a balance between innovation, intellectual property protection, and responsible practices. The art of reverse engineering continues to evolve, empowering us to unravel intricate systems and drive progress in the ever-advancing world of technology.