Breaking Down the Top 5 Java Security Vulnerabilities You Need to Patch ASAP
Discover the critical Java security vulnerabilities that demand immediate attention. Learn about…
Revolutionize Your Coding with Java Technology Stack: Tips and Tricks
Discover the power of Java technology stack with expert tips and tricks.…
Is Your Java Code Safe? Top 10 Vulnerabilities You Must Know
Discover the top 10 vulnerabilities that could jeopardize your Java code's security.…
Protecting Your Online World: 9 Special Roles of Message Digests in 2023
Explore the pivotal role of message digests in 2023 in safeguarding your…
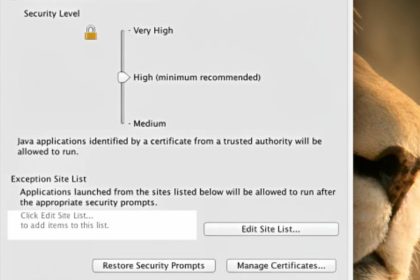
How to unblock applications blocked by java security ? | 9 Secrets to Unblocking Java Security Applications
Java has been a cornerstone of software development for decades, advertising flexibility,…
A Beginner’s Guide to LDAP Injection | 10 Reasons to Consider an LDAP Injection
Within the world of cybersecurity, understanding vulnerabilities and potential dangers is basic…
7 Best Free Full stack Java development courses for Beginners and Experienced Programmers in 2023
Java has long been a favorite programming dialect for its flexibility and…
Thirteen rules for developing secure Java applications | Top Essential Elements for Developing Secure Java Applications-Techearth
ava, with its vigor and flexibility, has gotten to be a prevalent…
Java vs. Dot Net | 9 Tips for Making Java Safer Than Dot Net
Within the domain of software advancement, two noticeable programming stages, Java and…
13 Essential Java Full Stack Developer Skills in 2023
The role of a Java Full Stack Developer has advanced altogether over…