Breaking Down the Top 5 Java Security Vulnerabilities You Need to Patch ASAP
Discover the critical Java security vulnerabilities that demand immediate attention. Learn about…
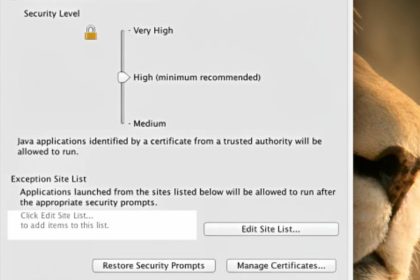
How to unblock applications blocked by java security ? | 9 Secrets to Unblocking Java Security Applications
Java has been a cornerstone of software development for decades, advertising flexibility,…
A Beginner’s Guide to LDAP Injection | 10 Reasons to Consider an LDAP Injection
Within the world of cybersecurity, understanding vulnerabilities and potential dangers is basic…
Thirteen rules for developing secure Java applications | Top Essential Elements for Developing Secure Java Applications-Techearth
ava, with its vigor and flexibility, has gotten to be a prevalent…
Java vs. Dot Net | 9 Tips for Making Java Safer Than Dot Net
Within the domain of software advancement, two noticeable programming stages, Java and…
Java Web Security: | How to Understand the Different Things to Consider About Web Security
Web security is a pivotal aspect of creating and deploying Java-based web…
Exploring Java 9-17 : A Comprehensive Guide| Why Is Java 9-17 Important?
Exploring Java 9-17: A Comprehensive Guide takes you on a journey through…
Java Security: An Investigation into the Risks
Within the tremendous and interconnected advanced domain, where information streams unreservedly and…